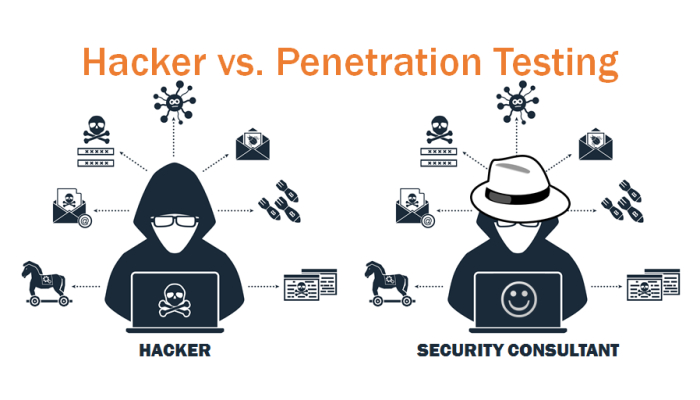
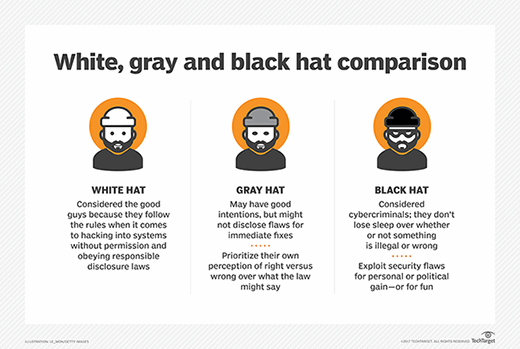
![White Hat Hacking and Penetration Testing | Tutorials [Downloadable HD Formatted The Complete Video Series - Learn Step By Step] - The Mental Club White Hat Hacking and Penetration Testing | Tutorials [Downloadable HD Formatted The Complete Video Series - Learn Step By Step] - The Mental Club](http://thementalclub.com/wp-content/uploads/2017/05/White-Hat-Hacking-and-Penetration-Testing-Tutorials.png)
White Hat Hacking and Penetration Testing | Tutorials [Downloadable HD Formatted The Complete Video Series - Learn Step By Step] - The Mental Club

ONLINE DELIVERY VIA EMAIL - Expert Training Advanced White Hat Hacking And Penetration Testing 15 Hour Video Course DOWNLOAD Downloadable Content: Buy ONLINE DELIVERY VIA EMAIL - Expert Training Advanced White Hat

Easy Learning Advanced White Hat Hacking And Penetration Testing Video Training DVD - Easy Learning : Flipkart.com
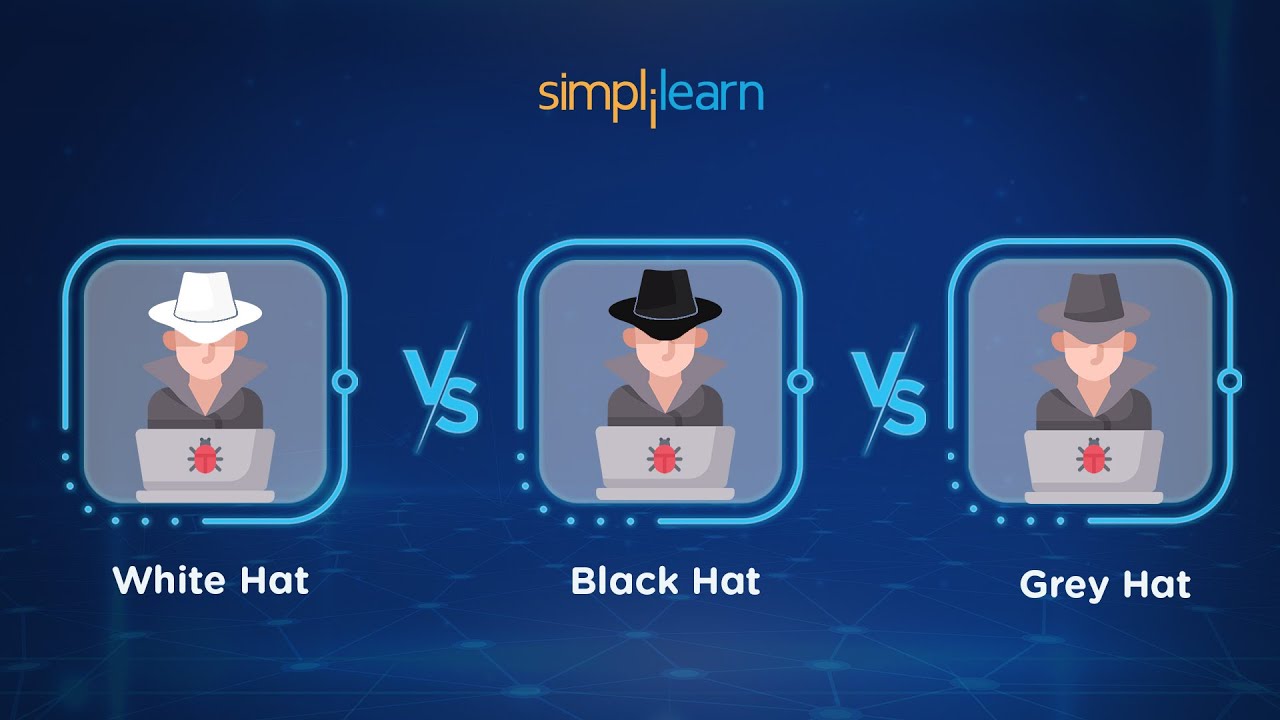
White Hat vs Black Hat vs Grey Hat | Types Of Hackers Explained | Ethical Hacking | Simplilearn - YouTube
What Is Ethical Hacking And What White Hacker Can Do For Cyber Security? | by Sravan Cynixit | Quick Code | Medium